Securing a SOAP API
| Mule Runtime Engine versions 3.5, 3.6, and 3.7 reached End of Life on or before January 25, 2020. For more information, contact your Customer Success Manager to determine how you can migrate to the latest Mule version. |
Enterprise
When a SOAP API exposes private-network data to the outside world, that data travels through four to seven separate protocol layers (TCP/IP or OSI) thus introducing potential security vulnerabilities. Implementing security at a higher layer on the protocol stack — the application layer, for instance — generally provides better protection than an implementation at the lower transport layer, which provides only HTTPS security.
To implement application-layer security, enable WS-Security on your SOAP API. WS-Security is a CXF configuration that defines a new SOAP header capable of carrying various security tokens that systems use to identify a API caller’s identity and privileges, and can include the following:
-
Encryption
-
Digital signature
-
Timestamp
Enabling WS-Security with Studio Visual Editor
To enable WS-security on a SOAP API in your application, you must add WS-configurations to the CXF Component in your flow. This approach enables WS-security locally within your flow, for one API only.
To the Mule flow that involves an API, add a CXF Component to publish, consume, or proxy an API. Complete the following steps to configure WS-security on the CXF component.
-
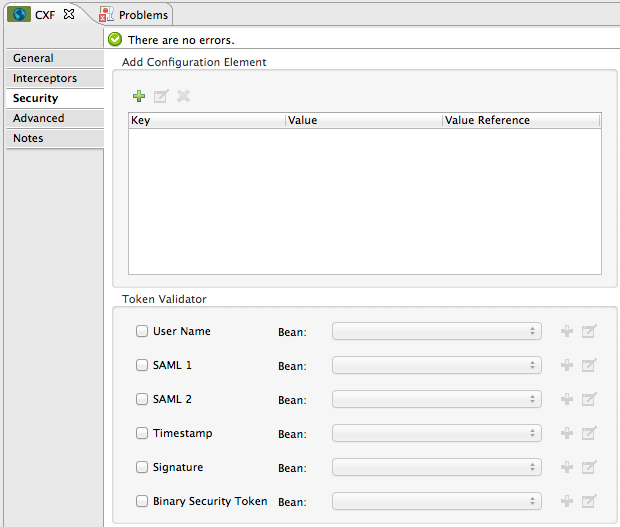
Open the properties editor, then click the Security tab.

-
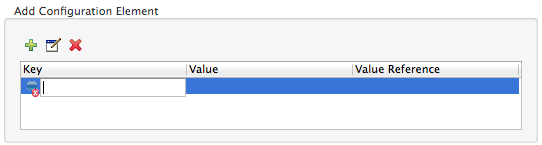
Click the plus sign icon in the Add Configuration Element pane to create a new key-value pair.
In XML, this step mirrors the addition of a key-value pair inside the
ws-configchild element of aws-securityelement. By adding configuration elements to your SOAP component, you are creating a map of key-value pairs that correspond to the CXF WSS4J security-configuration text strings in WSHandlerConstants and WSConstants. -
Enter a key, such as
action, in the open Key field and press Enter. -
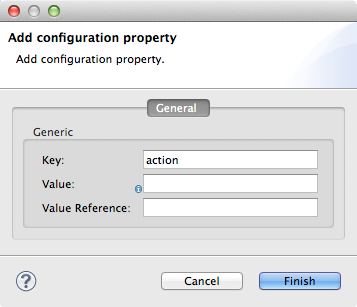
Double-click the new key-value line item you created to open the Add Configuration Property panel.
-
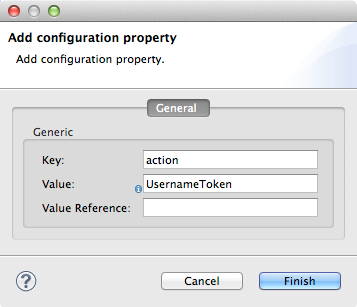
Enter information in either the Value field OR the Value Reference Field according to the table below.
Attribute Description Value
Enter a WS Constant (a class to define the kind of access the server allows) or a WSHandlerConstant (a class to specify the names, actions, and other strings for data deployment of the WSS handler). For example, enter
UsernameTokenin the value field.Value Reference
Enter the bean that the key must reference. When the key must reference a bean (for instance, when the key is
passwordCallbackRef), enter the name of the bean in the Value Reference field. -
Click Finish to save the key-value pair.
-
Repeat the steps above to add as many ws-security configurations as you wish to your API, then click OK to save your configurations.
Enabling WS-Security with Studio XML Editor or Standalone
To enable WS-security on a SOAP API in your application, you must add WS-configurations to the CXF Component in your flow. This approach enables WS-security locally within your flow, for one API only.
To the Mule flow that involves an API, add a CXF Component to publish, consume, or proxy an API. Complete the following steps to configure WS-security on the CXF component.
-
To your CXF element (that is, your SOAP component), add a child element for
cxf:ws-security. -
Within the
cxf:ws-securitychild element, add a child element forcxf:ws-config. -
Within the
cxf:ws-configchild element, add a child element forcxf:property. -
Add two attributes to the cxf:property child element according to the table below. Be sure to enter either a
value `OR a `value-ref; the two are mutually exclusive.Attribute Description key
Specify a name for the property.
value
Specify a WS Constant (a class to define the kind of access the server allows) or a WSHandlerConstant (a class to specify the names, actions, and other strings for data deployment of the WSS handler). For example, enter
UsernameTokenin the value field.value-ref
Specify the bean that the key must reference. When the key must reference a bean (for instance, when the key is
passwordCallbackRef), specify the name of the bean as the value-ref. -
Repeat the preceding step to add as many WS-security configurations as you wish to your API. Refer to sample code below.
<?xml version="1.0" encoding="UTF-8"?>
<mule xmlns:cxf="http://www.mulesoft.org/schema/mule/cxf"
xsi:schemaLocation="
http://www.mulesoft.org/schema/mule/cxf http://www.mulesoft.org/schema/mule/cxf/current/mule-cxf.xsd">
<http:listener-config name="listener-config" host="localhost" port="8081"/>
<flow name="Creation1Flow1" doc:name="Creation1Flow1">
<http:listener config-ref="listener-config" path="/" doc:name="HTTP Connector"/>
<cxf:jaxws-service doc:name="SOAP">
<cxf:ws-security>
<cxf:ws-config>
<cxf:property key="action" value="UsernameToken"/>
</cxf:ws-config>
</cxf:ws-security>
</cxf:jaxws-service>
</flow>Adding a Token Validator with Studio Visual Editor
If you have enabled WS-Security on your SOAP API in Mule, you can further configure the CXF component to delegate authentication of the message credentials it transmits or receives.
A CXF component may get bogged down with the tasks of both processing and authenticating messages. To lighten this load, you can instruct WS-security to delegate certain message authentication tasks to a Token Validator, including:
-
Validating the
UsernameTokenin cases where theCallbackHandlerimplementation does not have access to the password -
Validating the attributes of a received SAML assertion
-
Dispatching a received security token to a third-party security service for validation
Complete the following procedure to add token validators to your API.
-
In the Security tab of your SOAP component, click one or more of the check boxes to delegate message authentication tasks to token validators. Refer to the table below for the activity of each token validator.
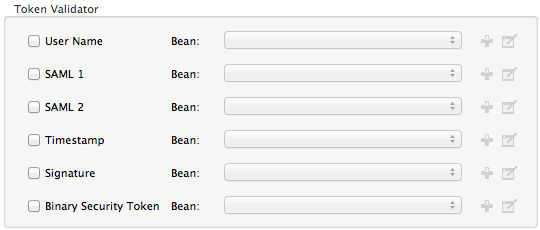
Token Validator Purpose User Name
Authenticates the username and password credentials associated with each message in a manner similar to HTTP Digest authentication.
SAML 1
Checks messages against SAML 1.1 assertion statements to approve or reject access to the API.
SAML 2
Checks messages against SAML 2.0 assertion statements to approve or reject access to the API. *Timestamp
Examines the timeliness of messages – when they were created and received, and when they expire – to make decisions about which messages to process.
Signature
Examines the digital signature attached to messages to make decisions about which messages to process.
Binary Security Token
-
In the Bean field associated with the token validator you have selected, use the drop-down menu to select an existing bean that your token validator will reference to apply, replace, or extend the default behavior associated with a specific security token.
-
If you have not created any beans, click the plus sign button to open a new properties panel in which you can create and configure a new bean. The bean imports the Java class you have built to specify the custom validator’s override behavior.
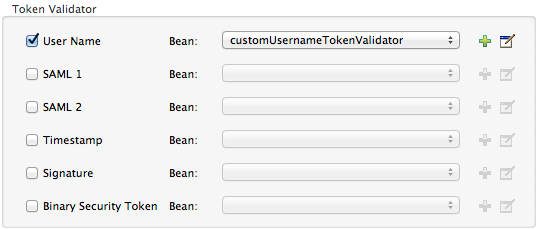
-
Click OK to save changes.
Adding a Token Validator with Studio XML Editor or Standalone
If you have enabled WS-Security on your SOAP API in Mule, you can further configure the CXF component to delegate authentication of the message credentials it transmits or receives.
A CXF component may get bogged down with the tasks of both processing and authenticating messages. To lighten this load, you can instruct WS-security to delegate certain message authentication tasks to a Token Validator, including:
-
Validating the
UsernameTokenin cases where theCallbackHandlerimplementation does not have access to the password. -
Validating the attributes of a received SAML assertion.
-
Dispatching a received security token to a third-party security service for validation.
Complete the following procedure to add token validators to your API.
-
Above all flows in your Mule project, create a global
spring:beanelement to import the Java class you have built to specify the token validator’s behavior. Refer to code sample below.View Java code for Bean Creation . To the CXF element in your flow, add a child element (below any `cxf:ws-config` elements you may have added) for `cxf:ws-custom-validator`. . To the `cxf:ws-custom-validator` child element, add a child element according to the type of action you want the validator to perform. Refer to the table below.
Token Validator Purpose cxf:username-token-validator
Authenticates the username and password credentials associated with each message in a manner similar to HTTP Digest authentication.
cxf:saml1-token-validator
Checks messages against SAML 1.1 assertion statements in order to approve or reject access to the API.
cxf:saml2-token-validator
Checks messages against SAML 2.0 assertion statements in order to approve or reject access to the API.
cxf:timestamp-token-validator
Examines the timeliness of messages – when they were created and received, and when they expire – to make decisions about which messages to process.
cxf:signature-token-validator
Examines the digital signature attached to messages to make decisions about which messages to process.
cxf:bst-token-validator
Examines binary encoded security tokens (such as Kerberos) to make decisions about which messages to process.
-
Add a
refattribute to the validator to reference the global spring:bean element which imports the Java class.
<?xml version="1.0" encoding="UTF-8"?>
<mule xmlns:cxf="http://www.mulesoft.org/schema/mule/cxf"
xsi:schemaLocation="
http://www.mulesoft.org/schema/mule/cxf http://www.mulesoft.org/schema/mule/cxf/current/mule-cxf.xsd">
<spring:beans>
<spring:bean id="customTokenValidator" name="Bean" class="org.mule.example.myClass"/>
</spring:beans>
<http:listener-config name="listener-config" host="localhost" port="8081"/>
<flow name="Creation1Flow1" doc:name="Creation1Flow1">
<http:listener config-ref="listener-config" path="/" doc:name="HTTP Connector"/>
<cxf:jaxws-service doc:name="SOAP">
<cxf:ws-security>
<cxf:ws-config>
<cxf:property key="action" value="UsernameToken"/>
</cxf:ws-config>
<cxf:ws-custom-validator>
<cxf:username-token-validator ref="Bean"/>
</cxf:ws-custom-validator>
</cxf:ws-security>
</cxf:jaxws-service>
</flow>Complete Code Example
<?xml version="1.0"?>
<mule xmlns="http://www.mulesoft.org/schema/mule/core" xmlns:core="http://www.mulesoft.org/schema/mule/core" xmlns:cxf="http://www.mulesoft.org/schema/mule/cxf" xmlns:doc="http://www.mulesoft.org/schema/mule/documentation" xmlns:http="http://www.mulesoft.org/schema/mule/http" xmlns:spring="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation=" http://www.mulesoft.org/schema/mule/http http://www.mulesoft.org/schema/mule/http/current/mule-http.xsd http://www.mulesoft.org/schema/mule/cxf http://www.mulesoft.org/schema/mule/cxf/current/mule-cxf.xsd http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans-current.xsd http://www.mulesoft.org/schema/mule/core http://www.mulesoft.org/schema/mule/core/current/mule.xsd ">
<spring:beans>
<spring:bean class="com.mulesoft.mule.example.security.SAMLCustomValidator" id="Bean" name="samlCustomValidator"/>
</spring:beans>
<http:listener-config name="listener-config" host="localhost" port="63081" basePath="services"/>
<flow doc:name="UnsecureServiceFlow" name="UnsecureServiceFlow">
<http:listener config-ref="listener-config" path="unsecure" doc:name="HTTP Connector"/>
<cxf:jaxws-service doc:name="Unsecure service" serviceClass="com.mulesoft.mule.example.security.Greeter"/>
<component class="com.mulesoft.mule.example.security.GreeterService" doc:name="Greeter Service"/>
</flow>
<flow doc:name="UsernameTokenServiceFlow" name="UsernameTokenServiceFlow">
<http:listener config-ref="listener-config" path="username" doc:name="HTTP Connector"/>
<cxf:jaxws-service doc:name="Secure UsernameToken service" serviceClass="com.mulesoft.mule.example.security.Greeter">
<cxf:ws-security>
<cxf:ws-config>
<cxf:property key="action" value="UsernameToken Timestamp"/>
<cxf:property key="passwordCallbackClass" value="com.mulesoft.mule.example.security.PasswordCallback"/>
</cxf:ws-config>
</cxf:ws-security>
</cxf:jaxws-service>
<component class="com.mulesoft.mule.example.security.GreeterService" doc:name="Greeter Service"/>
</flow>
<flow doc:name="UsernameTokenSignedServiceFlow" name="UsernameTokenSignedServiceFlow">
<http:listener config-ref="listener-config" path="signed" doc:name="HTTP Connector"/>
<cxf:jaxws-service doc:name="Secure UsernameToken Signed service" serviceClass="com.mulesoft.mule.example.security.Greeter">
<cxf:ws-security>
<cxf:ws-config>
<cxf:property key="action" value="UsernameToken Signature Timestamp"/>
<cxf:property key="signaturePropFile" value="wssecurity.properties"/>
<cxf:property key="passwordCallbackClass" value="com.mulesoft.mule.example.security.PasswordCallback"/>
</cxf:ws-config>
</cxf:ws-security>
</cxf:jaxws-service>
<component class="com.mulesoft.mule.example.security.GreeterService" doc:name="Greeter Service"/>
</flow>
<flow doc:name="UsernameTokenEncryptedServiceFlow" name="UsernameTokenEncryptedServiceFlow">
<http:listener config-ref="listener-config" path="encrypted" doc:name="HTTP Connector"/>
<cxf:jaxws-service doc:name="Secure UsernameToken Encrypted service" serviceClass="com.mulesoft.mule.example.security.Greeter">
<cxf:ws-security>
<cxf:ws-config>
<cxf:property key="action" value="UsernameToken Timestamp Encrypt"/>
<cxf:property key="decryptionPropFile" value="wssecurity.properties"/>
<cxf:property key="passwordCallbackClass" value="com.mulesoft.mule.example.security.PasswordCallback"/>
</cxf:ws-config>
</cxf:ws-security>
</cxf:jaxws-service>
<component class="com.mulesoft.mule.example.security.GreeterService" doc:name="Greeter Service"/>
</flow>
<flow doc:name="SamlTokenServiceFlow" name="SamlTokenServiceFlow">
<http:listener config-ref="listener-config" path="saml" doc:name="HTTP Connector"/>
<cxf:jaxws-service doc:name="Secure SAMLToken service" serviceClass="com.mulesoft.mule.example.security.Greeter">
<cxf:ws-security>
<cxf:ws-config>
<cxf:property key="action" value="SAMLTokenUnsigned Timestamp"/>
</cxf:ws-config>
<cxf:ws-custom-validator>
<cxf:saml2-token-validator ref="samlCustomValidator"/>
</cxf:ws-custom-validator>
</cxf:ws-security>
</cxf:jaxws-service>
<component class="com.mulesoft.mule.example.security.GreeterService" doc:name="Greeter Service"/>
</flow>
<flow doc:name="SignedSamlTokenServiceFlow" name="SignedSamlTokenServiceFlow">
<http:listener config-ref="listener-config" path="signedsaml" doc:name="HTTP Connector"/>
<cxf:jaxws-service doc:name="Secure SAMLToken Signed service" serviceClass="com.mulesoft.mule.example.security.Greeter">
<cxf:ws-security>
<cxf:ws-config>
<cxf:property key="action" value="SAMLTokenUnsigned Signature"/>
<cxf:property key="signaturePropFile" value="wssecurity.properties"/>
</cxf:ws-config>
<cxf:ws-custom-validator>
<cxf:saml2-token-validator ref="samlCustomValidator"/>
</cxf:ws-custom-validator>
</cxf:ws-security>
</cxf:jaxws-service>
<component class="com.mulesoft.mule.example.security.GreeterService" doc:name="Greeter Service"/>
</flow>
</mule>See Also
-
Learn more about configuring a CXF component in your Mule application.



